How to prevent Phishing

Phishing is a computer term that is associated with a particular type of nasty fraud.
Phishing is not to be confused with fishing but its name is chosen deliberately to conjure up images of fish being caught. Just like a fish, we can get tricked into clicking on a malicious link.
It works through the creation of an email or web page that looks like it belongs to a genuine company. It looks so real that the victim will not notice anything untoward. A typical phishing attack purports to be from your bank and the link that you use to visit your bank takes you to a perfect copy of your bank’s website.
So what is the purpose of this criminal activity?
Well, there are a variety of things that the criminal can be after. Most common is gaining valuable information such as your login credentials. As so many people use the same password for multiple sites, this is like gaining a master key set to just about everything. With so much of our transactions now online, your debit/credit card details are likely to be just a few keystrokes away.
If its not your finances they are after then personal information is great to use for spoofing. Yes, there is another favourite exploit of the cyber criminal. Spoofing is where the criminal manages to pass themselves off as someone else or they manage to pass their piece of software off as something else.
It won’t happen to me
You might think that this will never happen to you but these criminals know more than one trick. The best point of attack for them is when you are already concerned or overwhelmed by a particular problem.
A very level headed friend of mine fell victim to one of these attacks when he was having problems with his printer. Whilst he was getting increasingly annoyed with the issue, as he had better things to do with his time rather than fight printer driver software, a helpful dialog box popped up. I’m presuming that this happened whilst he was looking for help online but this dialog box looked like it was from the printer software.
He clicked on the “troubleshooting” button and it notified him of the Epson support helpline telephone number so he rang them up. Whilst he was talking to the guy on the phone, he must have clicked on something so that the guy “could take a look“ at his computer in order to get to the bottom of the printing issue. It was only when the guy told him that he had a virus on his machine and that it would cost £800 to get it removed that my friend hung up and quickly shut down his computer.
He didn’t know what software the fraudster used on his computer and if it is still there doing something…
Phishing Trends
Banks were the most often “phished” but now that cloud storage has become so popular, phishing using cloud storage companies as bait is even more prevalent. it’s the huge user base that attracts the fraudsters.
How can you safeguard against this?
There are a number of things that you can check that will help you to avoid being directed to a malicious website.
Check the email address of the sender.
Although it is possible to spoof an email address, often spoof addresses are detected by your ISP or mail client but not all providers are as good as each other.
However you can simply look at the “From” address and check that the part after the @ sign matches the domain name of the company it claims to be from. N.B. it is the part of the domain name that comes directly before the top level domain name.
e.g.
info@customersupport.paypal.com, unless spoofed, is coming a PayPal subdomain but
info@paypal.nastyhacker.com is not PayPal it is a subdomain of nastyhacker
If you don’t recognise the sender’s email address then do some research before you go further.
Check that the website is who they claim to be
When surfing the web, you find out more about the identity of a company that owns a website. You may not know if this site is trustworthy or not because you haven’t used it before. Just because you haven’t used it before doesn’t mean that there is any problem with it. But just like you would if you were to shop in the high street, you would want some assurance that they are at least who they say they are.
All browsers will identify if you are on a secure connection or not by checking for the SSL certificate. However, recently Google has changed its browser (Google Chrome) to flag up sites that do not use an SSL certificate as being untrustworthy. Well, that is true to a degree in that you need to have an SSL certificate in order to encrypt any data that it sent to or from the website. So sites that have a certificate will prevent hackers from gaining data that is submitted via a form, for example where you might be setting your password.
This is where it gets more interesting. Different certificates give you more information on the site you are visiting. The best certificates will verify that the company is actually who they say they are.
You can see if a site has a certificate by looking for the lock icon to the left of the address bar:
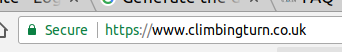
Standard SSL certificate
A Standard SSL certificate will give you 2048 bit encryption which protects users of the site from having their data intercepted and harvested by some unsavoury character. However, it does not prove that the site you are on is trustworthy.
Here is an example of a standard certificate, click on the lock icon to see further details. You can see that the Organisation is not part of the certificate.

Premium SSL certifcate
In order to obtain a premium SSL certificate an organisation needs to prove their identity as well as ownership of the domain. Documentation must be provided by the company in order to pass this verification.
This is a Premium certificate, notice the Organisation field is filled in.

EV Certificate
Extended verification. This guarantees the identity of the business as the documentation needed and personal verification is more extensive. When you apply for this type of certificate you need to be able to speak directly to the certificate authority. They will arrange a date with you to call you on your telephone number as published in a third party telephone listing such as the YellowPages, Scoot or 192.com. They will also need to know where your physical address and this is verified using an official registry such as Dun & Bradstreet.

An EV certificate has the name of the site in green just to the left of the address bar of your web browser. If you click on that green name then you can see more details about the certificate. In particular, you can see who owns the website.
Many browsers do not differentiate between standard and premium certificates because the only one that truly proves ownership is the EV certificate.
So next time you click on a link and are directed to a website, take a look at the address bar to see if they are who they say they are.
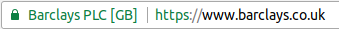

A Phishing site will not have an EV certificate proving that it is your bank or printer manufacturer.
Other blog items

Optimising ExpressionEngine
Caching, query optimisation, minimising tracking

ExpressionEngine CMS Updates
Why you should keep your ExpressionEngine Installation up to date
Organising ExpressionEngine Channels
How best to organise your content

AI automation and innovation
How can you leverage efficiency in the age of AI?

Tackling Immersive Harms
Innovate UK event 12th September 2024

Your Customers Need to Trust You
First impressions matter

AI UK 2024
The AI UK Conference held on the 19th and 20th of March 2024

Should you be selling something else?

Engage your website visitors
What is your number one service or product?

Teaching Ethics to AI
I will be back!
Blockchain Consensus for change
It's More than Just Crypto Currency

How AI Benefits Business
5 Business Benefits of AI

London Drum Company New Site Launch
Online Drum and Percussion Hire

How much do you share?
Privacy at a bus stop
Google Analytics
How to use MAMP (Mac Apache MySql php)
How to run multiple projects simultaneously with MAMP

Introducing BTR International
International move management services

DragonVet: a Hand-crafted Digital Presence
Make your message clear

How and Why has Launched
A website made to stand out from the crowd
Merlin Engine API builder
Get Ready… It’s Almost Here!

General Data Protection Regulation
This new regulation comes into enforcement on the 25th of May 2018.

Lasting Impressions for ExpressionEngine
Lasting Impressions is ExpressionEngine 4 ready!
Cyber Security
Five tips on how to keep your business safe
Is Your Website Rubbish?
How to measure its success online

Top tips to woo customers
Things that customers love

Top mistakes that lose you customers
Top 5 mistakes to avoid when publishing on the internet.

Is your Web Site Ready for Brexit?
Leaving the EU will bring both threats and opportunities

Primary School Children Code HTML

Curse of the Brochure Site
Missing the opportunity

A Web “Page”
It’s NOT a page!

Expression Engine MSM and CartThrob
Using the same channel to sell items on different sites

Exceptionally Dull Weirdos
This is a response to Willard Foxton's recent article on the Daily Telegraph blog

The Website Machine
What is a website?